Using GitHub Action
Running Bearer from the CLI is great, but if you want it integrated directly with your Git workflow there's nothing easier than a GitHub action. If you're unfamiliar with GitHub actions, here's a primer available from GitHub. You can also see how the action works directly on our Bear Publishing example app.
Getting started
You can view the action here, or follow along below.
Actions live in the .github/workflows/ directory within your repository. Start by creating a bearer.yml file in the workflows directory.
We recommend the following config in .github/workflows/bearer.yml to run Bearer's security report:
name: Bearer
on:
push:
branches:
- main
permissions:
contents: read
jobs:
rule_check:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Bearer
uses: bearer/bearer-action@v2
This will run the security report, show the report in the job log, and flag the action as pass or fail based on whether Bearer's default rules pass or fail.
Further configuration
Just as with the CLI app, you can configure the action to meet the needs of your project. Set custom inputs and outputs using the with key. Here's an example using the config-file, skip-path, and only-rule flags:
name: Bearer
on:
push:
branches:
- main
permissions:
contents: read
jobs:
rule_check:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Bearer
uses: bearer/bearer-action@v2
with:
config-file: "/some/path/bearer.yml"
only-rule: "ruby_lang_cookies,ruby_lang_http_post_insecure_with_data"
skip-path: "users/*.go,users/admin.sql"
Inputs
| Option | Description | Default |
|---|---|---|
| api-key | For use with Bearer Cloud | |
| bearer-ignore-file | bearer.ignore file path | |
| config-file | configuration file path | |
| diff | Enable differential scanning. Only supported for pull request events | false |
| exclude-fingerprint | Specify the comma-separated fingerprints of the findings you would like to exclude from the report. | |
| exit-code | Forces the exit-code when errors are reported | |
| format | Specify which format to use for the report (json, yaml, sarif, gitlab-sast) | |
| hide-progress-bar | Hide progress bar from output | true |
| only-rule | Specify the comma-separated ids of the rules you would like to run. Skips all other rules. | |
| output | Specify where to store the report | |
| path | The path to scan | . |
| quiet | Suppress non-essential messages | |
| scanner | Specify the comma separated scanners e.g. --scanner secrets,sast | |
| severity | Specify which severities are included in the report as a comma separated string | |
| skip-path | Specify the comma separated files and directories to skip. Supports * syntax, e.g. --skip-path users/*.go,users/admin.sql | |
| skip-rule | Specify the comma-separated ids of the rules you would like to skip. Runs all other rules. | |
| version | Specify the Bearer version to use. This must match a Bearer release name. |
Outputs
If you want to process the output of the cli we recommend using the output input above to write a file that can be used elsewhere, but we also provide some basic outputs you can use if needed:
| Option | Description | Default |
|---|---|---|
| exit_code | exit code from binary | |
| rule_breaches | Details of any rule breaches that occur |
Configure GitHub code scanning
Bearer CLI supports GitHub code scanning. By using the SARIF output format, you can display security report findings directly in the Security tab of your repository.
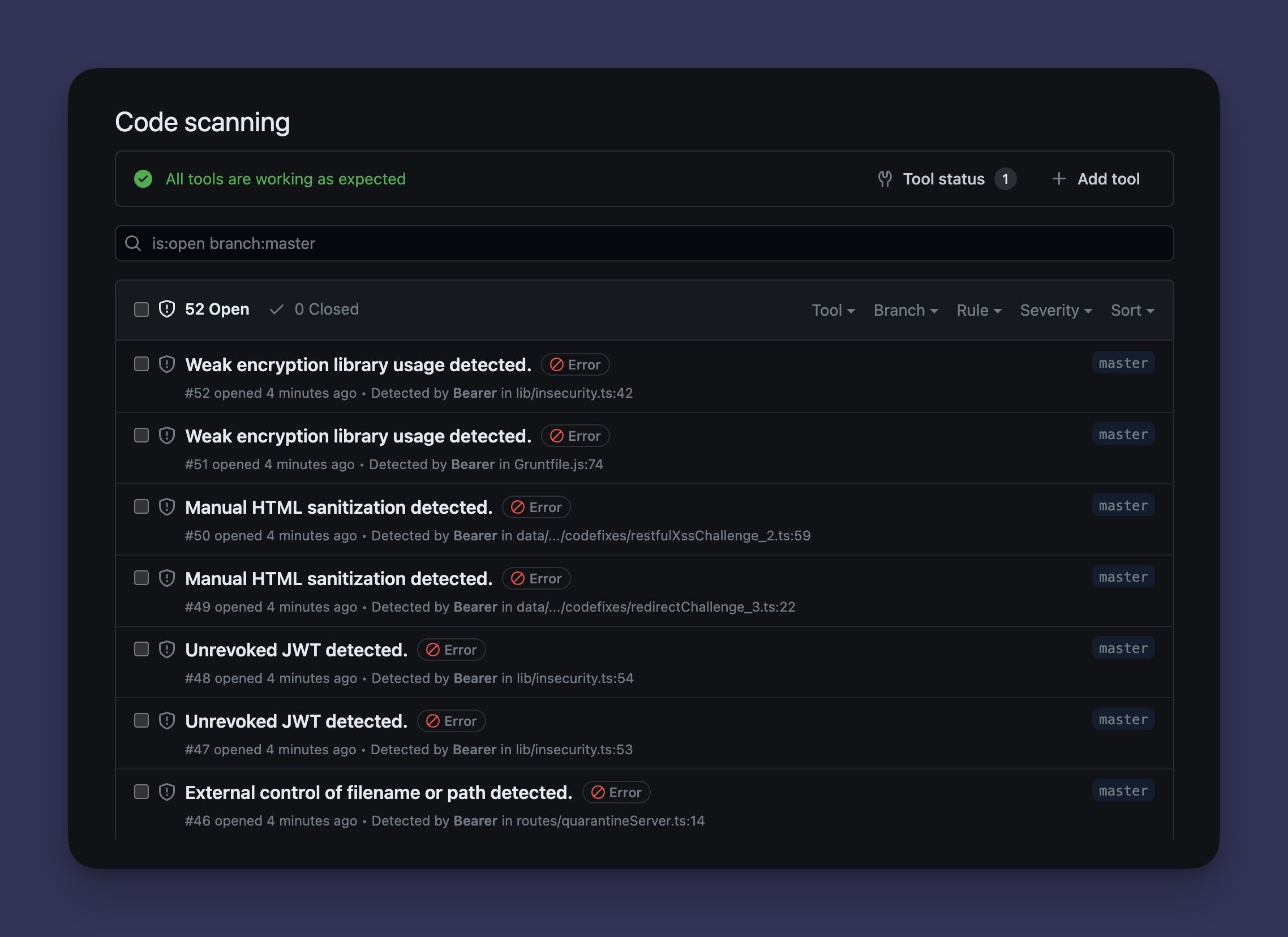
To enable this feature, update your action configuration to include new permissions, new format and outputs, and an additional step. Here's an example configuration:
name: Bearer
on:
push:
branches:
- main
permissions:
contents: read
jobs:
rule_check:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Bearer
uses: bearer/bearer-action@v2
with:
format: sarif
output: results.sarif
- name: Upload SARIF file
if: always()
uses: github/codeql-action/upload-sarif@v2
with:
sarif_file: results.sarif
By setting the format and output path, and adding a new upload step, the action will upload SARIF-formatted findings to GitHub's code scanner.
Pull Request Diff
When the Bearer action is being used to check a pull request, you can tell the
action to only report findings introduced within the pull request by setting
the diff input parameter to true.
name: Bearer PR Check
on:
pull_request:
types: [opened, synchronize, reopened]
permissions:
contents: read
jobs:
rule_check:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Bearer
uses: bearer/bearer-action@v2
with:
diff: true
See our guide on configuring a scan for more information on differential scans.
Code Review Comments
Bearer CLI supports Reviewdog rdjson format so you can use any of the reviewdog reporters to quickly add bearer feedback directly to your pull requests.
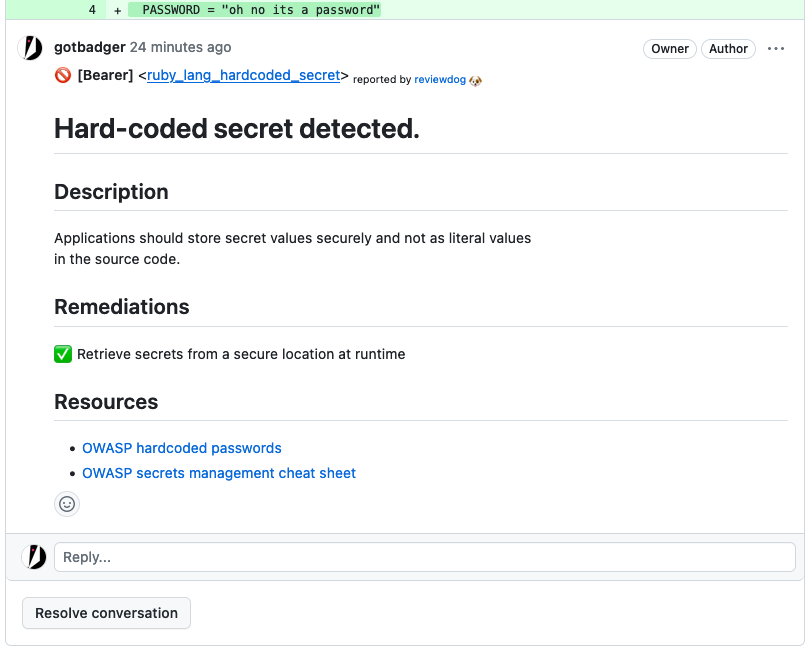
name: Bearer PR Check
on:
pull_request:
types: [opened, synchronize, reopened]
permissions:
contents: read
pull-requests: write
jobs:
rule_check:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- uses: reviewdog/action-setup@v1
with:
reviewdog_version: latest
- name: Bearer
uses: bearer/bearer-action@v2
with:
format: rdjson
output: rd.json
diff: true
- name: Run reviewdog
if: always()
env:
REVIEWDOG_GITHUB_API_TOKEN: ${{ secrets.GITHUB_TOKEN }}
run: |
cat rd.json | reviewdog -f=rdjson -reporter=github-pr-review
Integrate with Defect Dojo
We can monitor findings with Defect Dojo by using the gitlab-sast format and the v2 API. Make sure to update the instance url and set the necessary secrets.
name: Bearer Defect Dojo
on:
push:
branches:
- main
permissions:
contents: read
jobs:
rule_check:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Run Report
id: report
uses: bearer/bearer-action@v2
with:
format: gitlab-sast
output: gl-sast-report.json
- name: Defect Dojo
if: always()
env:
DD_TOKEN: ${{ secrets.DD_TOKEN}}
DD_APP: ${{ secrets.DD_APP}}
DD_ENGAGEMENT: ${{ secrets.DD_ENGAGEMENT}}
run: |
curl -X POST -F "file=@gl-sast-report.json" -F "product_name=$DD_APP" -F "engagement_name=$DD_ENGAGEMENT" -F "scan_type=GitLab SAST Report" -H "Authorization: Token $DD_TOKEN" http://example.com/api/v2/import-scan/
Make the most of Bearer
For more ways to use Bearer, check out the different report types, available rules, supported data types.
Have a question or need help? Please open an issue on GitHub.